- Category
- War in Ukraine
Russian Hackers Extorted Millions From Children’s Hospitals and Schools Worldwide
Russian nationals behind the hacker group "8Base,” extorted millions of dollars from victims—including children's hospitals—by holding sensitive data at ransom. Ransomware attacks on healthcare not only caused disruption but also put lives at risk. How did 8Base operate, and what does its downfall reveal about Russia’s cybercrime ecosystem?
Two Russian nationals, Roman Berezhnoy, 33, and Egor Nikolaevich Glebov, 39, have been arrested for leading a ransomware operation that targeted hospitals, healthcare providers, and schools, Europol reported.
Using a variant of Phobos ransomware , their groups, "8Base" and "Affiliate 2803," are suspected of extorting more than $16 million from over 1,000 victims between May 2019 and October 2024.
The hackers are alleged to have established and operated a darknet website where they repeated their threats and ultimately published the stolen data if a victim failed to pay the ransom.
Since 2022, the healthcare sector has been victim to an increased amount of cyber-attacks globally, which has not only caused disruption but led to life-threatening consequences.
Putin has built a corrupt mafia state driven by greed and ruthlessness. It is no surprise that the most unscrupulous extortionists and cyber-criminals run rampant from within his borders.
David Lammy
UK Foreign Secretary
How 8Base targeted healthcare and schools
8Base used Phobos which relies on high-volume attacks against small to medium-sized businesses, which often lack the cybersecurity defenses to protect themselves.
Ransomware is a type of malware that prevents you from accessing your device and the data stored on it, usually by encrypting your files.
As part of the scheme, Berezhnoy, Glebov, and others allegedly hacked into the victims' computer networks and copied and stole files. They then encrypted the original versions of the stolen data with Phobos ransomware, making the data inaccessible.
The conspirators would then allegedly demand ransom payments from the victims, in exchange for the decryption keys to regain access to the encrypted data. During Phobos ransomware attacks, ransom notes are normally left on the victim's computers to initiate ransom payment negotiations.
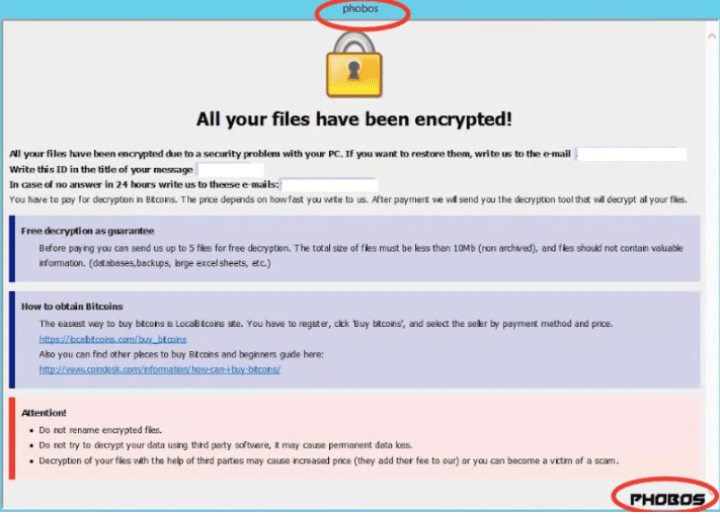
8Base developed its own variant of the ransomware, using its encryption and delivery mechanisms to tailor attacks for maximum impact, Europol reported.
“8Base has been particularly aggressive in its double extortion tactics, not only encrypting victims' data but also threatening to publish stolen information unless a ransom was paid,” Europol stated.
Law enforcement efforts investigating 8Base’s extortion network spanned multiple continents. Europol played a central role in assisting with the cross-border judicial cooperation between 14 countries, such as Czechia, France, and Germany, to Japan, Singapore, Thailand, and the US.
The charges against Berezhnoy and Glebov followed a recent arrest and extradition of Evgenii Ptitsyn, another Russian national, who was also charged for the alleged administration of the Phobos ransomware variant.
Ptitsyn is charged in a 13-count indictment with wire fraud conspiracy. He faces a maximum penalty of 20 years in prison for each wire fraud count; 10 years in prison for each computer hacking count; and five years in prison for conspiracy to commit computer fraud and abuse.
Berezhnoy and Glebov have been charged in an 11-count indictment, ranging from wire fraud conspiracy to conspiracy to commit computer fraud and abuse. If convicted, they face a maximum penalty of 20 years in prison on each wire fraud-related count, 10 years in prison on each computer damage count, and five years in prison on each of the other counts, Europol reported.
Life-threatening consequences
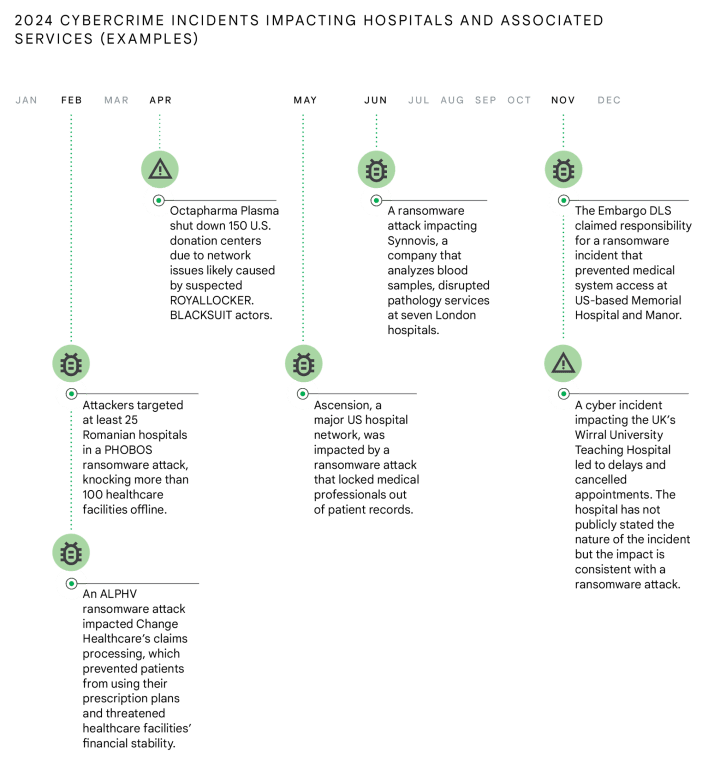
Since 2022, criminals have increasingly targeted and leaked data from hospitals, and Healthcare's share of posts on data leak sites has doubled over the past three years, Google Threat Intelligence Group (GTIG) published in their February 2025 “A Multifaceted National Security Threat” report.
Studies conducted by academics and hospital reviews show that ransomware attacks go beyond disruption but have led to life-threatening consequences for patients.
Cyberattacks on hospitals in several US states are currently underway. The World Economic Forum magically predicted this years ago. “Pay close attention to the frightening Scenario…of a Cyber Attack…” -Klaus Schwab pic.twitter.com/SZG46YSoJj
— Liz Churchill (@liz_churchill10) August 4, 2023
A recent study from researchers at the University of Minnesota, Twin Cities School of Public Health, showed that among patients already admitted to a hospital when a ransomware attack takes place, "in-hospital mortality increases by 35-41%."
A ransomware incident at a UK contractor in June 2024, led to multiple cases of "long-term or permanent impact on physical, mental or social function or shortening of life-expectancy," with more numerous cases of less severe effects UK National Health Service data showed.
Russia’s growing cybercrime
The UK Government announced on February 11, 2025, further sanctions against “a key Russian cybercrime syndicate responsible for aiding merciless ransomware attacks around the world.”
The sanctions have been placed against Russian entity ZSERVERS, 6 ZSERVERS members who are part of a prolific cybercrime supply chain, and their UK front company, XHOST.
“Predatory” ransomware groups generated $1 billion from their victims globally in 2023 alone, the UK government reported. ZSERVERS provides vital infrastructure for cybercriminals as they plan and execute attacks against the UK, the UK Government reported.
ZSERVERS explicitly advertise themselves to illicit actors as Bulletproof Hosting (BPH) Provider which is known to host hackers who share misinformation, child exploitation material, spam, and hate speech.
This government will continue to work with partners to constrain the Kremlin and the impact of Russia’s lawless cyber underworld. We must counter their actions at every opportunity to safeguard the UK’s national security and deliver on our Plan for Change.
David Lammy
UK Foreign Secretary
“Russia has drawn on criminal capabilities to fuel the cyber support to their war in Ukraine” GTIG reported. “GRU-linked APT44 (aka Sandworm), a unit of Russian military intelligence, has employed malware available from cybercrime communities to conduct espionage and disruptive operations in Ukraine.”
CIGAR, or the 'RomCom group' (aka Void Rabisu, Storm-0798) is a group known to conduct opportunistic ransomware and extortion operations and has conducted espionage operations against the Ukrainian government since 2022, according to GTIG.
GTIG noted that a high volume of cybercrime is not limited to Russia. Iranian threat groups deploy ransomware to raise funds while simultaneously conducting espionage, most notably, North Korea uses state-backed groups to directly generate revenue for the regime.
It is possible to retrieve data after being hacked?
“No More Ransom” is an initiative by the National High Tech Crime Unit of the Netherlands’ police, Europol’s European Cybercrime Centre, Kaspersky, and McAfee to help victims of ransomware retrieve their encrypted data without having to pay the criminals.
No More Ransom generally advises not to pay the ransom: “By sending your money to cybercriminals you’ll only confirm that ransomware works, and there’s no guarantee you’ll get the decryption key you need in return.”
No More Ransom highlights that cybercriminals will often attack where the highest profit can be made. In most cases, once a device is attacked, there is little to be done to regain access to the files unless the victim has a backup copy on another device.
No More Ransom states that it is sometimes possible to help infected users regain access to their encrypted files or locked systems, without having to pay by following their applications and advising users to see their guide for support.
“Cybercrime involves collaboration between disparate groups often across borders and without respect to sovereignty. Any solution requires international cooperation by both law enforcement and intelligence agencies to track, arrest, and prosecute these criminals,” said GTIG.
-46f6afa2f66d31ff3df8ea1a8f5524ec.jpg)




-347244f3d277553dbd8929da636a6354.jpg)

-f88628fa403b11af0b72ec7b062ce954.jpeg)