- Category
- War in Ukraine
Exposing the Identities of Russia’s “Digital Army”

Russia’s cyber army again attacked Ukrainian websites belonging to businesses involved in military repairs and production. Hacker groups pushing Russia’s propaganda narrative have relentlessly attacked Ukraine and its NATO Allies’ and now some of their members, have been identified.
Seven Ukrainian websites, including those of companies involved in military aircraft repairs and the production of military weapons and equipment, were hacked yesterday, January 5, 2025, by a pro-Russian hacker group, Noname057(16), as they claimed.
Since Russia’s full-scale invasion, Noname057(16) has been pushing pro-Russian narratives and propaganda while targeting government and commercial websites belonging to Ukraine and over 15 countries, mostly NATO members and Ukraine’s Allies’ with distributed denial of service (DDoS) attacks.
In a recent investigation, Molfar, an OSINT agency in Ukraine, unmasked the identity of several Russian hackers from Noname057(16) who are allegedly connected to, and being financed by Russian state structures.
Russia’s “digital army,” part of Moscow’s information war, consists of a wide range of actors, from pro-Russian hackers to the Kremlin and Russia’s IT organization, the Social Design Agency (SDA).
-9c3cee19ded0f41029d2ca3476513550.jpg)
Russia has persistently targeted Ukraine with DDoS attacks. On February 24, 2022, a DDoS attack began approximately one hour before Russia launched its major invasion of Ukraine against Viasat . The UK National Cyber Security Centre (NCSC) assessed that “Russia was almost certainly responsible for the attack.”
“We will continue to call out Russia’s malign behavior and unprovoked aggression across land, sea, and cyberspace, and ensure it faces severe consequences”, Liz Truss, the then UK Foreign Secretary said.
In the first year-and-a-half of Russia’s full-scale war, almost 4,000 cyberattacks were recorded by Ukraine's Computer Emergency Response Team (CERT-UA) a US Treasury Department official stated.
DDoS attacks aim to disrupt service, often making websites and critical business applications unavailable and grinding operations and productivity to a halt.
Hacktivists? Call us whatever you want, the important thing is that you respect us and fear us.
Who is Noname057?
Russian Cyber Army / Noname057(16) are two hacker groups that have merged into one. They have been conducting cyber attacks against Ukraine and NATO countries since 2022 and are likely funded by Russian state structures, Molfar stated. Users who provide resources to them are rewarded with cryptocurrency.
Molfar found Artem Vladimirovich Pankratov, a Russian national, to be a likely key member of Noname057(16). Molfar says that he administers their Telegram group and the Noname057(16) X account belongs to him where he regularly boasts about successful hacks, and shares Russian propaganda via social media while following groups like “Russian idea.”

In an interview in January 2025, Noname057(17) repeat several well-known Russian propaganda agendas. They call Russia’s full-scale invasion of Ukraine, a “Russian special military operation,” and they call Ukrainians neo-nazis while repeating quotes from Alexander Blok, a Russian poet known for “Russian symbolism.”
Pankratov’s wife, Yuliya Vladimirovna Pankratova is listed on the Myrotvorets as a “Russian war criminal” and an “employee of An employee of the Russian special services”.
The US imposed sanctions on Yuliya and Denis Olegovich Degtyarenko (Degtyarenko), “two members of the Russian hacktivist group Cyber Army of Russia Reborn (CARR) for their roles in cyber operations against US critical infrastructure,” the US Department of the Treasury reported in July 2024.
“Pankratova, also known as YUliYA online, is a Russian cybercriminal and the leader of CARR. Pankratova commands and controls CARR’s operations. Pankratova has acted as a spokesperson for CARR” the US Department of the Treasury reported.
She administers the Telegram channel of the Russian hacker community DDoSia, Molfar reported operating under the nickname “MotherOfbears” and is active in groups associated with Russian propaganda.

This morning, January 6, 2025, Noname057(16) claimed to have launched a DDoS attack against French government sites including the French Ministry of Justice, after Deputy Director of the Foundation for Strategic Studies, Bruno Tertrais, said in an interview with Ukrinform that France could send a peacekeeping force to Ukraine in the presence of a hypothetical ceasefire agreement. Pankratov called them “French Russophobes”.
On January 5, 2025, the hacker group claimed via their X account “@Noname05716” to have hacked 7 Ukrainian websites, mainly those belonging to organizations involved in military assets including:
Ukroboronprom – Strategic partner for the production of weapons and military equipment in Ukraine.
Zaporizhzhia State Aviation Repair Plant “MiGremont” – for aircraft such as MiG-25, Su-25, Su-27.
Antonov JSC – a Ukrainian state-owned enterprise engaged in air cargo operations, development, production, and repair of AN series aircraft, part of the Ukrainian Defense Industry.
JSC Kyiv Radar Plant - specialized in the manufacture of modern radar and radio navigation.
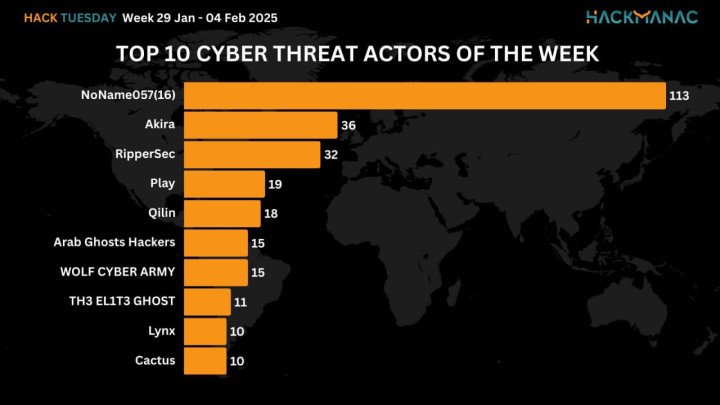
Between January 29 to February 4, 2025, Noname057 conducted 113 cyber-attacks according to HackManc.
The Guardia Civil arrested three Noname057(16) cybercriminals in Manacor, Huelva, and Seville In July 2024. “Despite being considered a hacktivist organization, their past ties with the Russian Federal Security Service (FSB) and their high level of organization with other pro-Russian hacktivist groups have made them a very active player in the international scene,” the Spanish National Cybersecurity Institute reported.
#OperacionesGC | Tres detenidos por delitos de daños
— Guardia Civil (@guardiacivil) July 20, 2024
informáticos con fines terroristas.
Habrían participado voluntariamente en la realización
de ataques de denegación de servicios organizados por el grupo hacktivista NoName057(16)#GuardiaCivil pic.twitter.com/1Py28lIUkp
“Suspending services for a day or even hours causes huge economic losses, if a facility is idle, it's losing money-critical infrastructure too,” Ted, a man in charge of the IT Army in Ukraine, a group working to counter Russian attacks, told UNITED24 Media. “Huge investments are made in cybersecurity to protect them, these are dollars not spent on war. Economic losses are not just due to temporary termination of facilities, but protecting them as well.”
What is the IT Army of Ukraine?
IT Army of Ukraine was initially referred to as “hacktivists” but Ted says this is the wrong description and they think of themselves as a classic volunteering organization with a specialty in conducting offensive operations in cyberspace.
He gave us an example of how their cyber attacks work. “During the missile attack on Crimea, we switched off some internet providers, assuming that they supplied CCTV information to Russian forces. So, we made it difficult for them to counter those attacks.”
“The Western world applied sanctions to make Russia weaker economically-we do the same, we work as a kind of sub-operation which extends sanctions further, creating economic damage, making them (Russia) suffer and incapable to keep financing war and the supply chain within it,” Ted said.
He told UNITED24 Media that they never target healthcare or humanitarian missions, but mainly finance and infrastructure. “Digital infrastructure is a huge vulnerability for nearly every modern country such as Russia and Iran. If you're going to fight a strong enemy and you want to survive, you've got to exhaust them. We go beyond enemy lines. If you do nothing towards death, you’ve got to defend in other ways, and if you're weaker by default, you will lose. The only question is when.”
-46f6afa2f66d31ff3df8ea1a8f5524ec.jpg)
-9377b86f9f8cd8a2b08f20ffd5f043e0.jpg)


-29a1a43aba23f9bb779a1ac8b98d2121.jpeg)
-5568db4fb3d8644b8f1bf8244594bec1.png)

